Insights
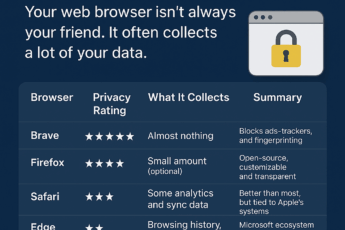
Know your web browsers
If you care about your privacy — and you should — here’s something a lot of people don’t realize: Your web browser (Chrome, Edge, Safari) isn’t always your friend. It’s often the biggest collector of your data. Most of them are quietly gathering your information in the background: what you click, what you search for,...... Read More
Your Business Website Might Be Wide Open to Cyberattacks — Here’s How to Protect It
Most small business owners wouldn’t dream of leaving their store unlocked overnight — but many are unknowingly doing exactly that online. Your website is your digital storefront. If it’s not secured, hackers can walk right in, steal valuable data, plant malicious software, and damage your reputation. Unfortunately, this isn’t a rare problem. We’ve seen local...... Read More
The Heart-Stopping Reality of Healthcare Cyber Attacks
Imagine a life-or-death situation where hospital staff are tending to an emergency patient, only to discover that all systems are disabled due to a ransomware attack. This is a nightmare scenario that healthcare organizations must be prepared for. Ransomware attacks are on the rise, and the healthcare industry is particularly vulnerable. These attacks involve hackers...... Read More
Unleash the Power: Install Kali Linux on Your Windows Desktop with VMware
Kali Linux, a powerhouse for penetration testing and security auditing, can now be at your fingertips within a safe and controlled environment on your Windows machine. Here’s how to install Kali Linux on a virtual machine using VMware Workstation Player, making it readily accessible from your Windows desktop. Prerequisites: VMware Workstation Player: Download and install the...... Read More
RAID Done Right: Choosing the Champion for Your Data
Data. It’s the lifeblood of our digital world, and keeping it safe is paramount. But with ever-growing storage needs and the constant threat of drive failure, traditional single disks just don’t cut it anymore. Enter RAID, the guardian angel of data storage! RAID (Redundant Array of Independent Disks) combines multiple disks into a single logical...... Read More
VPN Showdown: Unveiling the Strengths and Weaknesses of Different Protocols
VPNs are like suits of armor for your online data, but just like armor, there are different types, each with its own strengths and weaknesses. Let’s delve into the most common VPN protocols and see which one best suits your digital jousting needs: 1. OpenVPN: The Customizable Champion Strengths: OpenVPN reigns supreme in customization and security....... Read More
Building a Moat Around Your Data: The Power of Network Segmentation
Imagine your network as a sprawling medieval kingdom. A single breach in the wall could leave your entire realm vulnerable. Network segmentation is like building a series of fortified castles within your kingdom, creating multiple layers of defense to shield your most valuable assets. In the world of cybersecurity, network segmentation is the practice of...... Read More
Don’t Be Bullied By The Brute: How to Defend Against Brute Force Attacks
In the digital world, our accounts are like our front doors – we lock them to keep unwanted visitors out. But just like a determined burglar might try every key on their ring, hackers can use a brute force attack to crack your passwords and gain access to your personal information. So, what exactly is...... Read More
What is SQL Injection and how to defend against it
SQL injection attacks are a sneaky way for attackers to manipulate database queries run by a web application. Here’s a breakdown of how they work: Vulnerable Application: Imagine a web form that asks you for your username and password to log in. Ideally, the application should treat this information as data and separate it from...... Read More
Nature’s Soundtrack to Your Success: Focus Boost with Soothing Sounds
Feeling your concentration fading in the silence of your workspace? You’re not alone. While absolute quiet might seem ideal for intense work, our brains often crave more. The answer? Dive into the surprisingly effective world of listening to nature sounds while you work. It’s not just a whimsical notion. Studies reveal that nature’s gentle melodies...... Read More