LLMNR Poisoning: Understanding and Mitigating the Risk
The LLMNR Poisoning Attack In today’s interconnected world, network security is more crucial than ever. One vulnerability is LLMNR (Link-Local Multicast Name Resolution) Poisoning attacks. These attacks allow malicious actors to intercept and manipulate network traffic, compromising sensitive information. How LLMNR and NBT-NS Work To understand the attack, let’s first explore how LLMNR and NBT-NS...... Read More
Spear Phishing Detection with Splunk
In the previous walkthrough, Uncovering Hidden Threats with Splunk, we discovered that a threat actor was probing our organization’s website, froth.ly during the reconnaissance stage of their attack. We learned that they successfully accessed and downloaded an unsecured spreadsheet file containing the contact information of the organization’s employees. With this information, the threat-actor can launch...... Read More
Uncovering Hidden Threats with Splunk
Reconnaissance is the initial phase of cyber threat hunting, where hunters gather information about the network, systems, and potential vulnerabilities. This phase is critical in identifying potential entry points for attackers and understanding the attack surface. Effective reconnaissance involves analyzing network traffic, system logs, and endpoint data to identify anomalies and potential security gaps. In...... Read More
A Guide to Generating and Managing SSH Keypairs for Remote Access
Secure remote access is essential for system administrators and developers, and SSH (Secure Shell) keys offer a robust method for authentication. This guide will walk you through generating an SSH keypair on Kali Linux, adding it to a remote machine, and managing it across multiple systems. To begin, you need to generate an SSH keypair....... Read More
The Heart-Stopping Reality of Healthcare Cyber Attacks
Imagine a life-or-death situation where hospital staff are tending to an emergency patient, only to discover that all systems are disabled due to a ransomware attack. This is a nightmare scenario that healthcare organizations must be prepared for. Ransomware attacks are on the rise, and the healthcare industry is particularly vulnerable. These attacks involve hackers...... Read More
Installing Splunk Enterprise on Kali Linux
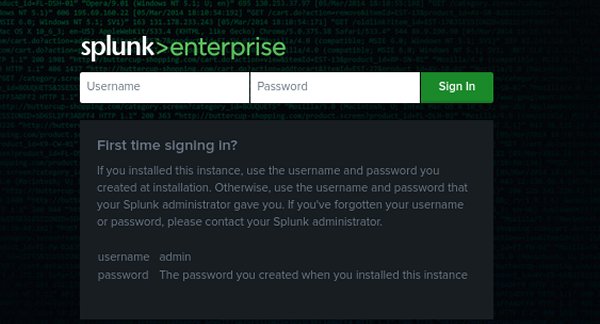
This is a basic tutorial on how to install the free-trial version of Splunk Enterprise on your Kali Linux machine. At the time of writing, splunk-9.3.0-51ccf43db5bd-linux-2.6-amd64.deb is the most recent kernal. Your install might be a different file name. Signup for Free trial of Splunk – https://www.splunk.com/en_us/download/splunk-enterprise.html Download the installation package. Choose .deb if you...... Read More
Securing the Digital Age: A Look at Cryptography Algorithms
In our increasingly digital world, protecting information is paramount. Cryptography algorithms form the backbone of this security, scrambling data to ensure confidentiality and integrity. This article dives deep into the world of cryptography algorithms, exploring their types, uses, strengths, and weaknesses. Unveiling the Cryptographic Arsenal: Key Types Cryptography algorithms fall into three main categories, each...... Read More
Unleash the Power: Install Kali Linux on Your Windows Desktop with VMware
Kali Linux, a powerhouse for penetration testing and security auditing, can now be at your fingertips within a safe and controlled environment on your Windows machine. Here’s how to install Kali Linux on a virtual machine using VMware Workstation Player, making it readily accessible from your Windows desktop. Prerequisites: VMware Workstation Player: Download and install the...... Read More
RAID Done Right: Choosing the Champion for Your Data
Data. It’s the lifeblood of our digital world, and keeping it safe is paramount. But with ever-growing storage needs and the constant threat of drive failure, traditional single disks just don’t cut it anymore. Enter RAID, the guardian angel of data storage! RAID (Redundant Array of Independent Disks) combines multiple disks into a single logical...... Read More
VPN Showdown: Unveiling the Strengths and Weaknesses of Different Protocols
VPNs are like suits of armor for your online data, but just like armor, there are different types, each with its own strengths and weaknesses. Let’s delve into the most common VPN protocols and see which one best suits your digital jousting needs: 1. OpenVPN: The Customizable Champion Strengths: OpenVPN reigns supreme in customization and security....... Read More